The IoT and the Serious Security Risks It Poses
Introduction
The Internet of Things (IOT) refers to the increasingly networked world we now inhabit, in which more and more “smart” devices use Internet to interact with other devices, servers, or with various users. It is not a new type of Internet, but an evolutionary development that shows how incremental technology growth can lead to major business and societal changes.
The Internet has changed the way we do research, the way we buy things, and the way we interact, among other thing, and thus the nature of society. This has resulted from the poliferation of computers and smart devices, as well as ever cheaper and more available bandwidth. The Internet upended many business models and led to the explosion of social media; but up to now it has been primarily a person-to-server or person-to-person mechanism. The proliferation of smart devices is in the process of changing that paradigm, since much of the communication of these devices is with other devices or servers. There are many devices that can be connected and interact, on scales ranging from tiny low-power sensors to high-power devices with powerful CPUs and large memory. IoT spans this range. But therein lies the problem: IoT devices, while “smart”, may not be smart enough because of the evolving nature of Internet security threats!
There are two main issues:
- Simple devices with simple operating systems are vulnerable to takeover and being turned into “zombies”, i.e., used for purposes other than what was intended
- Devices with more sophisticated operating systems, such as Windows, which are not updated regularly and thus can fall victim to the same threat as that in (1). Users of personal devices are constantly nagged about updates; many IoT devices are “set it up and forget it”—there is no one to nag.
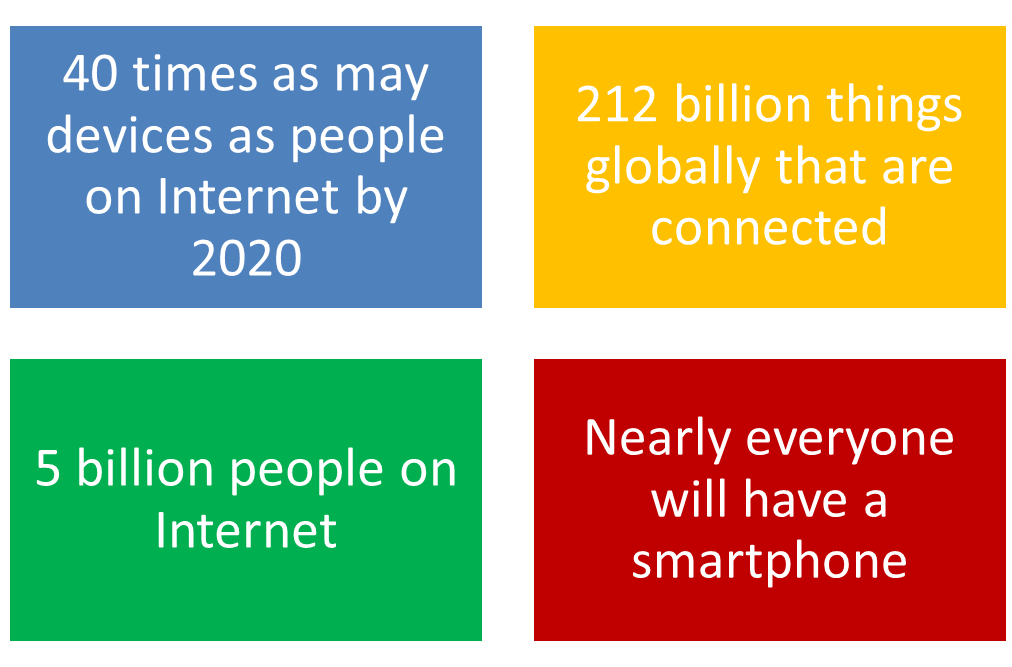
Why is this a potentially serious problem? There has been explosive growth in connected devices, as shown in Figure 1.
Figure 1. Growth in Connected Devices
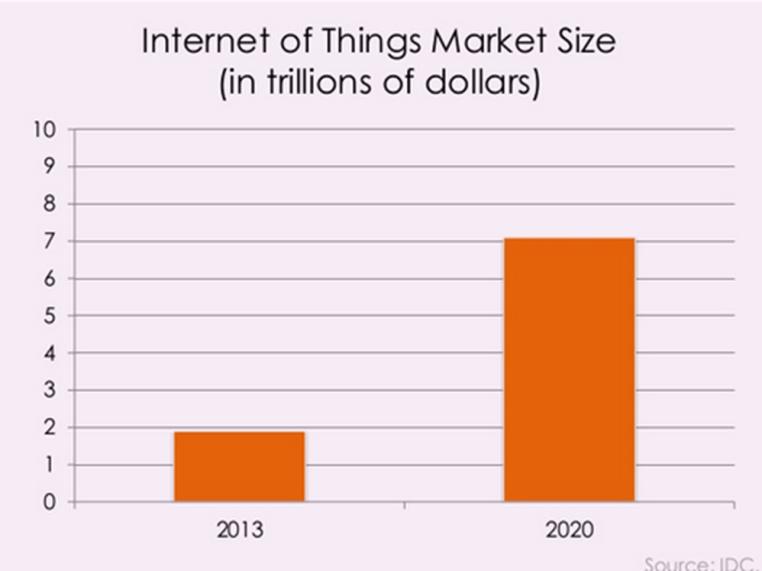
With 40 times as many devices as people, and 212 billion devices, if even a small fraction are compromised, a great deal of damage can be done. With IoT, there is no person involved and the devices talk to each other. It is therefore much more difficult to determine when a device has been compromised. Of course the hardware to allow machines to send data over the Internet has been around for a long time. What is changing is the ubiquity of these machines, the low cost of the Internet interface, our increasing use of IoT devices to take over tasks that we used to do manually, using connections over networks, and the increased security risks that this represents. The IoT marketplace is expected to grow dramatically over the next few years, as shown in Figure 2.
Figure 2. Market Size for IoT
Hacking, ransomware, and cyber extortion are becoming big business; the IoT is likely to make these problems worse because of the increased avenues for mischief. It might be much easier for a hacker to penetrate a corporate network by going after a lowly IoT device than after a server protected with layers of security software. These hacks can be done by individuals and state entities, and they are likely to increase over time, with more types of machines potentially vulnerable. Though some (in)famous hacks of the recent past, such as the Chinese-based OPM hack of 2015, were not done through IoT devices, future penetration attempts are much more likely to try this route. If voting machines, for example, are connected to the Internet (very few if any now are), they of course could become targets, with significant political consequences. The 2017 Equifax hack, which exposed the financial and personal data of nearly half the U.S. population, shows the scale of the danger.
IoT and Other New Technologies
Machine-to-Machine (M2M) Communication
One of the new technologies forming part of the Internet of Things (IoT) is Machine-to-Machine (M2M) communications. M2M, though not well-defined, is a set of methods and protocols to allow devices to communicate and interact over the Internet (or other network) without human intervention. M2M is sometimes considered to be low-overhead short-range wireless communication between machines, utilizing protocols with much less overhead than full-blown TCP/IP. Many M2M applications involve low power wireless devices with limited computing power and narrowly-defined functionality. Low-overhead protocols have been devised for them, including Message Queue Telemetry Transport (MQTT), Constrained Application Protocol (CoAP), and Open Mobile Alliance Light Weight M2M (OMA LWM2M). CoAP is actually a specialized web transfer protocol designed for applications such as smart energy and building automation.
These applications promise many benefits, but the very simplicity of these devices, and their widespread deployment, implies that if their software can be compromised, many systems can be taken out of service for an extended period, and the devices can be programmed to cause congestion on parts of the Internet, at the very least. If millions of M2M (or other IoT) devices are found to be vulnerable, replacing or reprogramming them could be very costly and time-consuming. If they are compromised and bring down important systems, such as patient monitoring systems, the effects could be catastrophic for many people.
Wireless Sensor Networks (WSNs)
IoT configurations often involve sensors, which can be connected by wireless networks. Such sensor networks are called Wireless Sensor Networks (WSNs). A WSN comprises spatially distributed autonomous devices equipped with sensors, connected through a wireless network to some type of gateway. The sensors typically monitor physical or environmental conditions. The gateway communicates with another set of devices that can act on the information from the sensors. Application examples include patient monitoring; environmental monitoring of air, water, and soil; structural monitoring for buildings and bridges; industrial machine monitoring; and process monitoring. The wireless network could be WiFi or Bluetooth, and the protocol one of the three listed above.
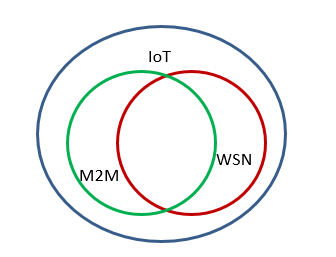
The boundaries between these networks are not clearly drawn, and in practice they overlap considerably. Figure 3 shows the relationship schematically:
Figure 3. Relationship of IoT, M2M, and WSN
For the purposes of our discussion, we will regard M2M and WSN as being a part of IoT.
IoT’s Goals
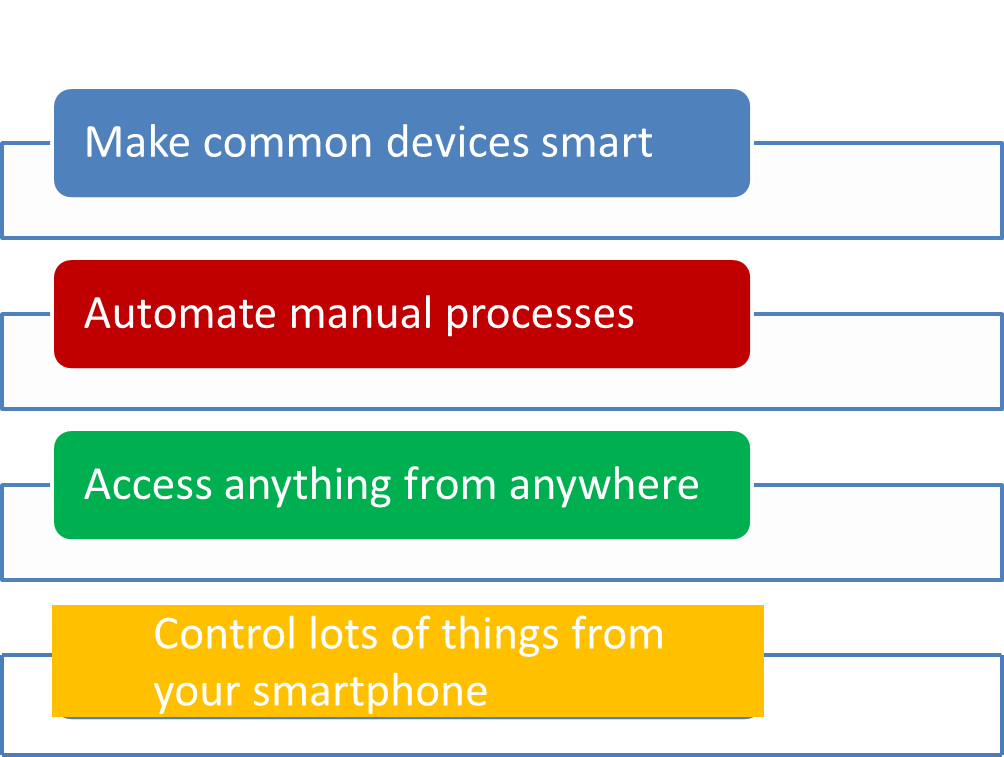
In the short term, at least, the goals of IoT are straightforward, as illustrated in Figure 4:
Figure 4. Goals of IoT
The objectives revolve around efforts to reduce costs and save time. They also promise to make new things possible that are not feasible now, such as devices for improved patient monitoring and improved transportation systems utilizing autonomous vehicles and other modes. But if security issues cannot be resolved, the risks associated with many applications will be unacceptable and will kill or delay the applications.
IoT Enabling Technologies
There are many technologies that support IoT and make possible its steady advance. A partial list includes the following:
- Cheap and ubiquitous telecommunications
- Smart software
- Smart devices
- Cheap memory
- Cheap and extremely powerful microprocessors
- Cloud Computing
- Big Data, Event Stream Processing, Real-Time Analytics
- Machine Learning
- Wireless sensor networks
- Low power short-range and wide area wireless networks
- Embedded Systems
- Automation and Control Systems
- Existing and emerging telecom technologies: Li-Fi, LPWAN, LTE-Advanced, 5G, WiFi-Direct, BLE, Low Energy, ZigBee, Z-Wave, Thread, HaLow, …
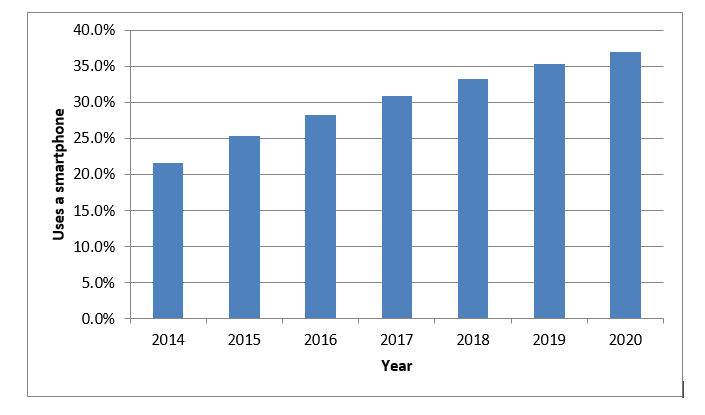
Few of these are radically new; most represent ongoing improvements to existing equipment and software. IoT is one of the beneficiaries of these continual improvements and cost reductions. Smartphones, for example, are clearly central to many IoT applications. The rapid growth of these devices is one driver for IoT:
Figure 5. Global Smartphone User Penetration as Percentage of Total World Population (2017-2020 data are estimates)
An increasing percentage of the world now uses smartphones to connect to the Internet.
Understanding the Vision of IoT
IoT can be understood on three levels:
- At the lowest or most basic level, IoT just connects simple devices over the Internet or some other network, which could be private and/or wireless. Common examples already in widespread use are programmable thermostats (change your house temperature at anytime from anywhere in the world) and security systems. Most modern security systems allow you to monitor your home security cameras over the Internet with a special App. Here is a typical system, this one by Honeywell and sold (of course) over the Internet by Amazon:
Figure 6. Home Thermostat Control over Internet
- At the mid-level, IoT is an enabler of new business and technology models, not just incremental improvement of existing models. For example, autonomous vehicles will require very high levels of communication among devices in the vehicle (e.g., LIDAR, sensors, cameras, computers) and most likely devices/sensors outside the vehicle (e.g., other vehicles, fixed cameras, servers with detailed maps).
- At the highest level, the interconnection of devices could lead, over time, to new types of technologies that will reorganize society, much as the automobile and the Internet have done. One possibility is the “Smart City”, where IoT is used not only in autonomous vehicles, but where all types of transportation are linked to provide optimized people movement. Private self-driving cars, in this scenario, would rarely be needed. This could lead to entirely different land use patterns, for example.
For each of these levels there is a corresponding security concern:
- At the lowest level, if a hacker can determine how to break into, say, the Honeywell thermostats, just as a bad joke, the hacker could drastically overheat or overcool the house or turn the heat off on a cold winter day, leading to burst pipes and tens of thousands of dollars in damage.
- At the mid-level, autonomous cars will rely on many communications systems, including sensors and systems outside the vehicle itself. If these can be hacked in such a way as to allow the autonomous car to be commandeered, then complete chaos can ensue on the roads, along with many fatal accidents.
- At the highest level, the “smart city” could essentially be shut down. Just the ability to turn off traffic lights is enough to cause complete gridlock in a very short period of time.
At all three levels, hackers could resort to extortion (similar to but potentially more serious than the recent ransomware attacks) because of the threat of major disruption.
IoT Application Areas
There are many possible application areas for IoT. Just to name a few, consider:
- Retail
- Healthcare
- Wearables
- Smart Home
- Smart Cities
- Intelligent Transportation
- Smart Grid
- Smart Agriculture
- Smart Industry
- Energy Management
Here are two examples:
Figure 7. Smart Sprinkler Control over the Internet
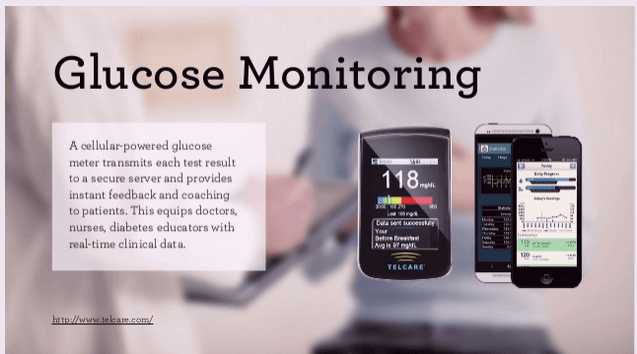
Smart sprinkler control is a rather obvious idea; this model is from lono.io. The following glucose monitoring system from www.telcare.com could be extremely beneficial to many diabetes patients:
Figure 8. Glucose Monitoring Using Smart Devices
Security
Obviously the future viability of IoT will depend on the degree of security attainable. The more we automate the systems upon which we rely for our daily life, the more vulnerable we become. Already this is an issue not only with autonomous cars—where the potential for mischief is obvious—but even with cars already on the road, due to their computerized infrastructure that can be controlled, to some extent at least, by wireless signals. Control of vehicles by hackers reportedly has already happened. And what if a hacker took over your car (with you in it) and drove it to a remote location, where you were forced to give him your bank account information or your car would go over a cliff?
Here’s the Wall Street Journal writing about the large Sept. 2016 cyberattack that utilized smart devices, the type employed by IoT systems:
Attackers used an army of hijacked security cameras and video recorders to launch several massive internet attacks last week, prompting fresh concern about the vulnerability of millions of “smart” devices in homes and businesses connected to the internet … Experts have long warned that machines without their own screens are less likely to receive fixes designed to protect them. (“Hackers Infect Army of Cameras, DVRs for Massive Internet Attacks”, Drew Fitzgerald, WSJ, 29 September 2016)
That is, people tend to forget about smart devices, and the more out-of-sight smart devices there are in the IoT, the more vulnerable we become. This problem is, I’m afraid, not receiving as much attention at this moment as it should, and this will probably take many years to fix. Of course, 20 years ago, when the Internet was just getting started as a commercial venture, security wasn’t given much thought either. But there is a difference if we don’t have a screen with which to interact with smart devices. When was the last time that you updated the firmware in your thermostat, or for that matter, your car?
Any mid- or high-level IoT-mediated changes will require new security paradigms, and these paradigms will no doubt add overhead to the IoT, and may slow its deployment.
So what can be done? It is very difficult for any single person or company to defend against all possible threats, especially since some (such as attacks on civic infrastructure) would have nothing to do with an individual’s or a company’s actions or systems. The problem, of course, has to be attacked on multiple fronts.
- Individuals and companies can avoid deployment of IoT systems that do not have upgradable software or firmware, and that do not have a scheduled plan for doing such upgrades to allow for security enhancements.
- These systems should be designed so that they can either run autonomously (i.e., disconnected from the Internet) for a certain period of time, or can be shut down altogether and their functions taken over manually in an emergency.
- Systems such as autonomous cars need a fail-safe mechanism that can sense malfunction or takeover, and cause the vehicle to pull over and stop.
- Dependence on IoT devices and systems should never be allowed to reach the point where no one really knows what they are doing. Even without hacking, in this case, feedback loops could develop that essentially paralyze the entire operation. The July 2017 incident involving “Steve”, a security robot on patrol outside a Washington, DC office complex that “went nuts” and drowned itself in a fountain is a comical illustration of the real dangers that lurk. In the case of autonomous cars travelling at 60 mph, it would not be so comical.
- Software and operating systems allowed for use on the Internet (or even private IP networks) should have to pass strict certification. This might pose problems for the simplest IoT devices, but will pay security dividends in the future.
- All devices connected to the Internet should have an “expiration date”, such that after that date, they no longer function. Such expiration dates are common on food items and drugs, so the concept is not unfamiliar. The idea would be that no outdated devices, which pose the greatest risk, are left up indefinitely.
- Networks, such as company networks, should be partitioned so as to allow walling off part of the network in the event of a problem. This can be done through physical wiring or through IP addresses.
- A world-wide database of devices that have been successfully hacked should be made available, so that companies and individuals can determine if they are at risk. Ideally, the companies and individuals can have an inventory of their devices that is periodically (e.g., daily) checked against this database.
- Passwords are known to have many problems as a security measure. The main problem is that humans are not good at memorizing hundreds of passwords—and nearly every web site involving commerce or personal data requires one. The inevitable result is that the same password is used for all or most sites, and it is often written on a piece of paper taped to the monitor! New means need to be implemented, taking advantage of advances in biometrics, such as fingerprint and facial recognition, iris/retina scanning, and voice prints.
As with crime in the real world, it will never be possible to completely eliminate security problems in cyberspace. The only realistic goal is to keep the problems and damage to a minimal and manageable level. This will require vigilance and close attention to the nine steps above, at the very least.
Summary
The Internet of Things is coming and indeed in some ways is already here. It encompasses the networking and interaction of smart devices to achieve functionality that is currently labor-intensive, inconvenient, or just not feasible. It has begun with small-scale smart devices, and is progressing through larger, more complex systems such as autonomous vehicles. At some point in the future, the scope and degree of the automation may result in changes in major areas of society such as living and transportation, similar to those resulting from the automobile and the Internet. However, a major barrier to all of these applications is security, because anyone who can seize control of networked devices can create havoc and even cause personal injury or death. Steps should be taken now at the individual, corporate, and national/global level to minimize security risks.
Editor’s Note: Check out the Eogogics IoT courses including the course on IoT Security.





Sorry, comments for this entry are closed at this time.